|
|
||
|---|---|---|
| .devcontainer | ||
| .github | ||
| .vscode | ||
| build | ||
| client | ||
| docs | ||
| images | ||
| server | ||
| .dockerignore | ||
| .gitignore | ||
| Dockerfile | ||
| LICENSE | ||
| docker-compose.yml | ||
| docker-template.xml | ||
| index.js | ||
| package-lock.json | ||
| package.json | ||
| prod.js | ||
| readme.md | ||
readme.md
About
Audiobookshelf is a self-hosted audiobook and podcast server.
Features
- Fully open-source, including the android & iOS app (in beta)
- Stream all audio formats on the fly
- Search and add podcasts to download episodes w/ auto-download
- Multi-user support w/ custom permissions
- Keeps progress per user and syncs across devices
- Auto-detects library updates, no need to re-scan
- Upload books and podcasts w/ bulk upload drag and drop folders
- Backup your metadata + automated daily backups
- Progressive Web App (PWA)
- Chromecast support on the web app and android app
- Fetch metadata and cover art from several sources
- Chapter editor and chapter lookup (using Audnexus API)
- Merge your audio files into a single m4b
- Embed metadata and cover image into your audio files (using Tone)
- Basic ebook support and e-reader (experimental)
Is there a feature you are looking for? Suggest it
Android App (beta)
Try it out on the Google Play Store
iOS App (early beta)
Available using Test Flight: https://testflight.apple.com/join/wiic7QIW - Join the discussion

Organizing your audiobooks
Directory structure and folder names are important to Audiobookshelf!
See documentation for supported directory structure, folder naming conventions, and audio file metadata usage.
Installation
Docker Install
Available in Unraid Community Apps
docker pull ghcr.io/advplyr/audiobookshelf:latest
docker run -d \
-e AUDIOBOOKSHELF_UID=99 \
-e AUDIOBOOKSHELF_GID=100 \
-p 13378:80 \
-v </path/to/audiobooks>:/audiobooks \
-v </path/to/podcasts>:/podcasts \
-v </path/to/config>:/config \
-v </path/to/metadata>:/metadata \
--name audiobookshelf \
ghcr.io/advplyr/audiobookshelf:latest
Docker Update
docker stop audiobookshelf
docker rm audiobookshelf
docker pull ghcr.io/advplyr/audiobookshelf:latest
docker start audiobookshelf
Running with Docker Compose
### docker-compose.yml ###
services:
audiobookshelf:
container_name: audiobookshelf
image: ghcr.io/advplyr/audiobookshelf:latest
environment:
- AUDIOBOOKSHELF_UID=99
- AUDIOBOOKSHELF_GID=100
ports:
- 13378:80
volumes:
- </path/to/audiobooks>:/audiobooks
- </path/to/podcasts>:/podcasts
- </path/to/config>:/config
- </path/to/metadata>:/metadata
Docker Compose Update
Depending on the version of Docker Compose please run one of the two commands. If not sure on which version you are running you can run the following command and check.
Version Check
docker-compose --version or docker compose version
v2 Update
docker compose --file <path/to/config>/docker-compose.yml pull
docker compose --file <path/to/config>/docker-compose.yml up -d
V1 Update
docker-compose --file <path/to/config>/docker-compose.yml pull
docker-compose --file <path/to/config>/docker-compose.yml up -d
Linux (amd64) Install
Debian package will use this config file /etc/default/audiobookshelf if exists. The install will create a user and group named audiobookshelf.
Ubuntu Install via PPA
A PPA is hosted on github
See install docs
Install via debian package
Get the deb file from the github repo.
See install docs
Linux file locations
Project directory: /usr/share/audiobookshelf/
Config file: /etc/default/audiobookshelf
System Service: /lib/systemd/system/audiobookshelf.service
Ffmpeg static build: /usr/lib/audiobookshelf-ffmpeg/
Reverse Proxy Set Up
Important! Audiobookshelf requires a websocket connection.
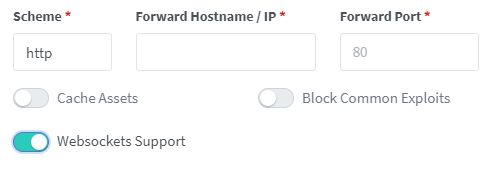
NGINX Proxy Manager
Toggle websockets support.
NGINX Reverse Proxy
Add this to the site config file on your nginx server after you have changed the relevant parts in the <> brackets, and inserted your certificate paths.
server
{
listen 443 ssl;
server_name <sub>.<domain>.<tld>;
access_log /var/log/nginx/audiobookshelf.access.log;
error_log /var/log/nginx/audiobookshelf.error.log;
ssl_certificate /path/to/certificate;
ssl_certificate_key /path/to/key;
location / {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $host;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_http_version 1.1;
proxy_pass http://<URL_to_forward_to>;
proxy_redirect http:// https://;
}
}
Apache Reverse Proxy
Add this to the site config file on your Apache server after you have changed the relevant parts in the <> brackets, and inserted your certificate paths.
For this to work you must enable at least the following mods using a2enmod:
sslproxy_moduleproxy_wstunnel_modulerewrite_module
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName <sub>.<domain>.<tld>
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
ProxyPreserveHost On
ProxyPass / http://localhost:<audiobookshelf_port>/
RewriteEngine on
RewriteCond %{HTTP:Upgrade} websocket [NC]
RewriteCond %{HTTP:Connection} upgrade [NC]
RewriteRule ^/?(.*) "ws://localhost:<audiobookshelf_port>/$1" [P,L]
# unless you're doing something special this should be generated by a
# tool like certbot by let's encrypt
SSLCertificateFile /path/to/cert/file
SSLCertificateKeyFile /path/to/key/file
</VirtualHost>
</IfModule>
SWAG Reverse Proxy
Synology Reverse Proxy
- Open Control Panel > Application Portal
- Change to the Reverse Proxy tab
- Select the proxy rule for which you want to enable Websockets and click on Edit
- Change to the "Custom Header" tab
- Click Create > WebSocket
- Click Save
Traefik Reverse Proxy
Middleware relating to CORS will cause the app to report Unknown Error when logging in. To prevent this don't apply any of the following headers to the router for this site:
- accessControlAllowMethods
- accessControlAllowOriginList
- accessControlMaxAge
From @Dondochaka and @BeastleeUK
Forward Proxy Authentication
Users can be authenticated via an external proxy such as Authentik. To use forward authentication you need to set the following environment variables:
PROXY_FORWARD_AUTH_ENABLED- enable/disable forward authenticationPROXY_FORWARD_AUTH_USERNAME- the name of the header containing the authenticated user's username. For example, by default in Authentik the value would beX-authentik-username.PROXY_FORWARD_AUTH_CREATE- automatically create users if they don't exist (with account type ofuser).PROXY_FORWARD_AUTH_LOGOUT_URI- path to redirect to when logging out.
